Contents:
- Objectives
- Create VPC
- Create Subnets
- Create Internet Gateway
- Create NAT Gateway
- Create Route Tables
- Create Security Groups
- Expected Result
Objectives
- Create a dedicated VPC for the application.
- Split Public Subnets and Private Subnets across 2 Availability Zones (Multi-AZ).
- Set up Internet Gateway, NAT Gateway, and Route Tables to ensure:
- Public Subnets can access the Internet (for ALB, NAT).
- Private Subnets can access the Internet via NAT Gateway (for Fargate Tasks to pull images, call APIs, etc.).
- Prepare Security Groups to control network traffic.
Create VPC
- Go to VPC Console → Create VPC
- Choose:
- Name tag:
fargate-workshop-vpc - IPv4 CIDR:
10.0.0.0/16 - Tenancy: Default
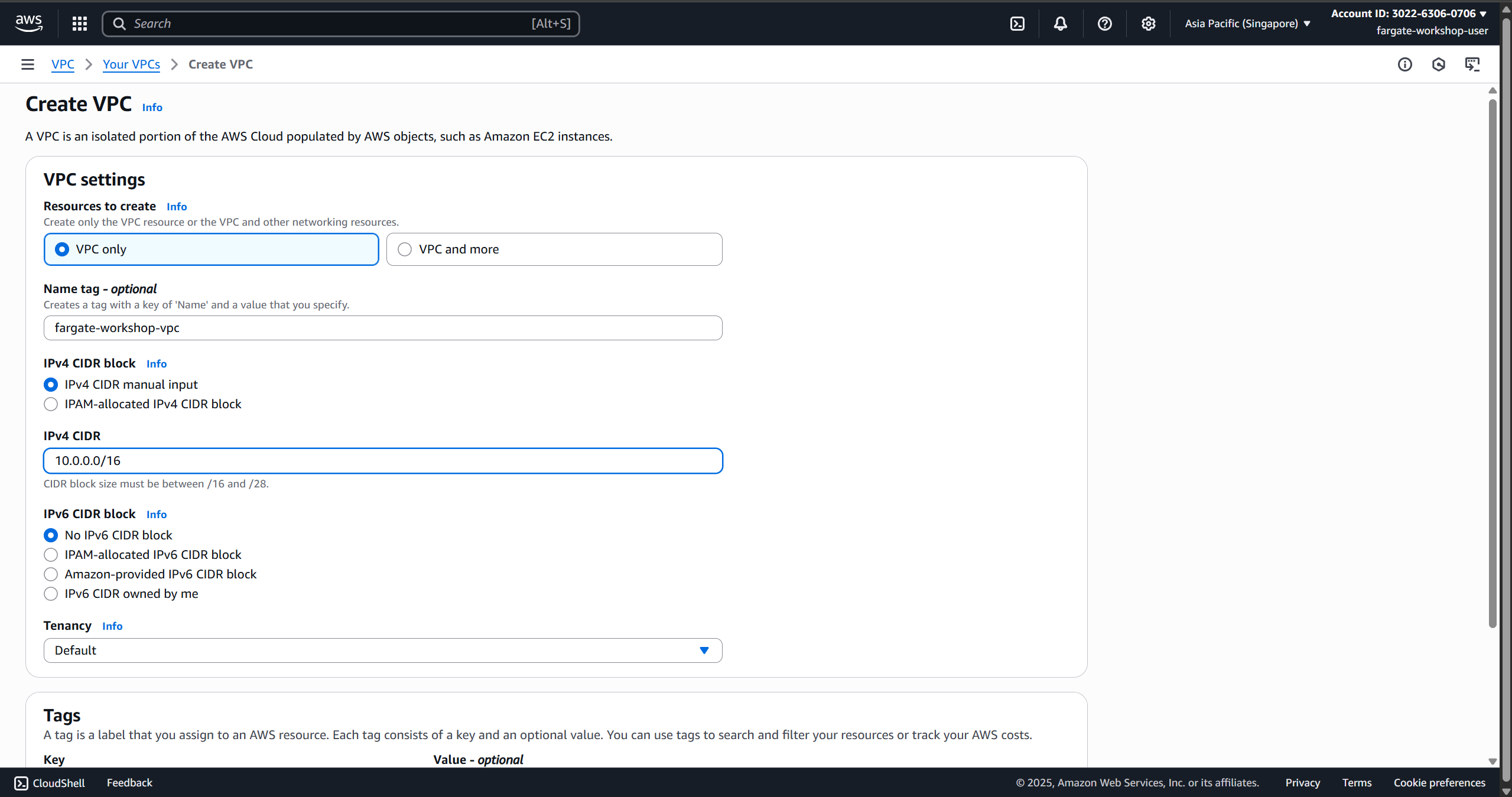
- Name tag:
Create Subnets
- Go to Subnets → Create subnet
- Select the newly created VPC
- Create 4 subnets:
- Public Subnet 1:
10.0.1.0/24(AZ1) - Private Subnet 1:
10.0.3.0/24(AZ1) - Public Subnet 2:
10.0.2.0/24(AZ2) - Private Subnet 2:
10.0.4.0/24(AZ2)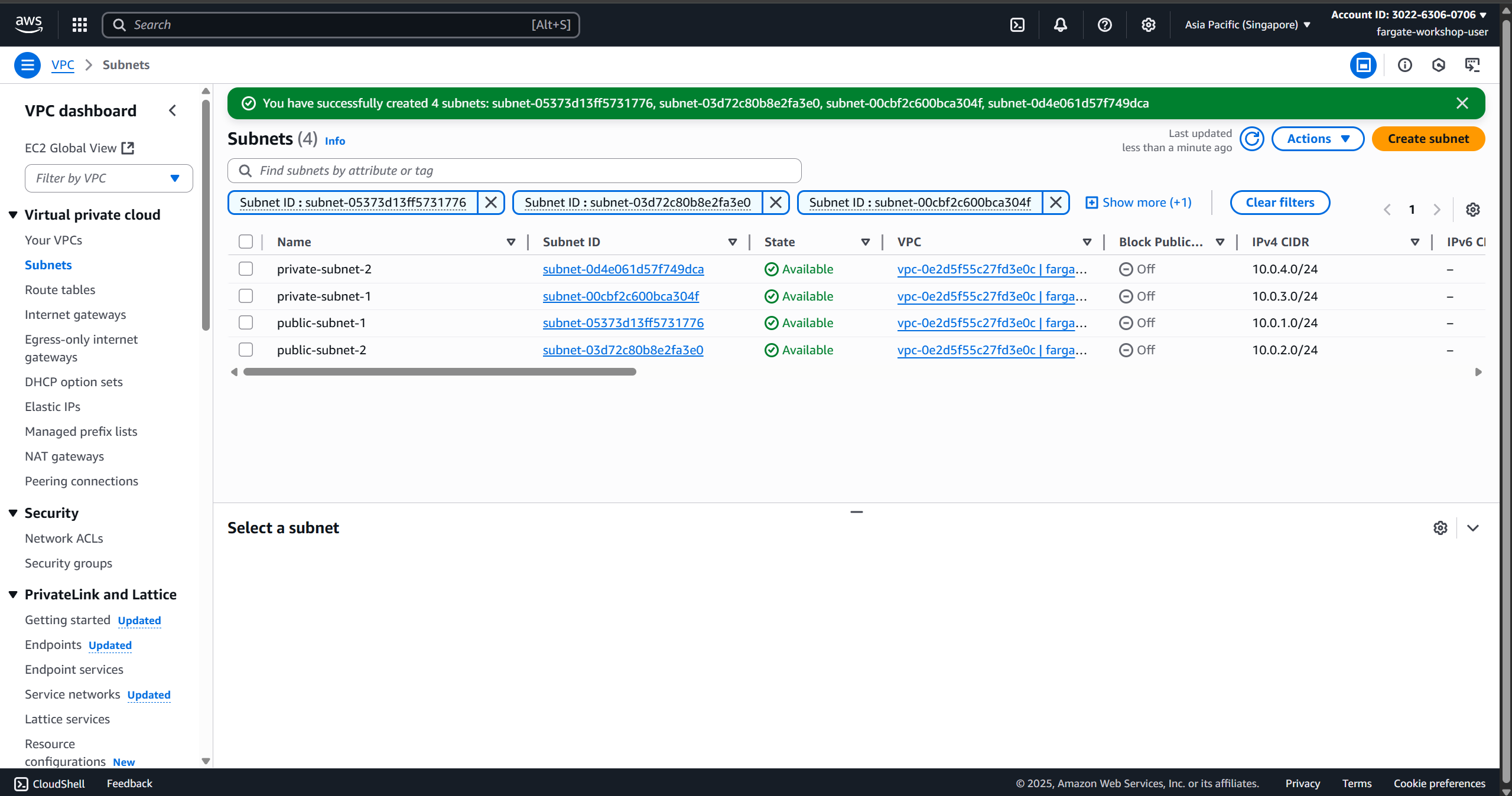
- Public Subnet 1:
Create Internet Gateway
- Go to Internet Gateways → Create IGW
- Name:
fargate-igw - Attach it to the newly created VPC
Create NAT Gateway
- Go to NAT Gateways → Create NAT Gateway
- Select:
- Public Subnet 1 (AZ1)
- Allocate Elastic IP
- Create a second NAT Gateway for Public Subnet 2 (AZ2) for High Availability
Create Route Tables
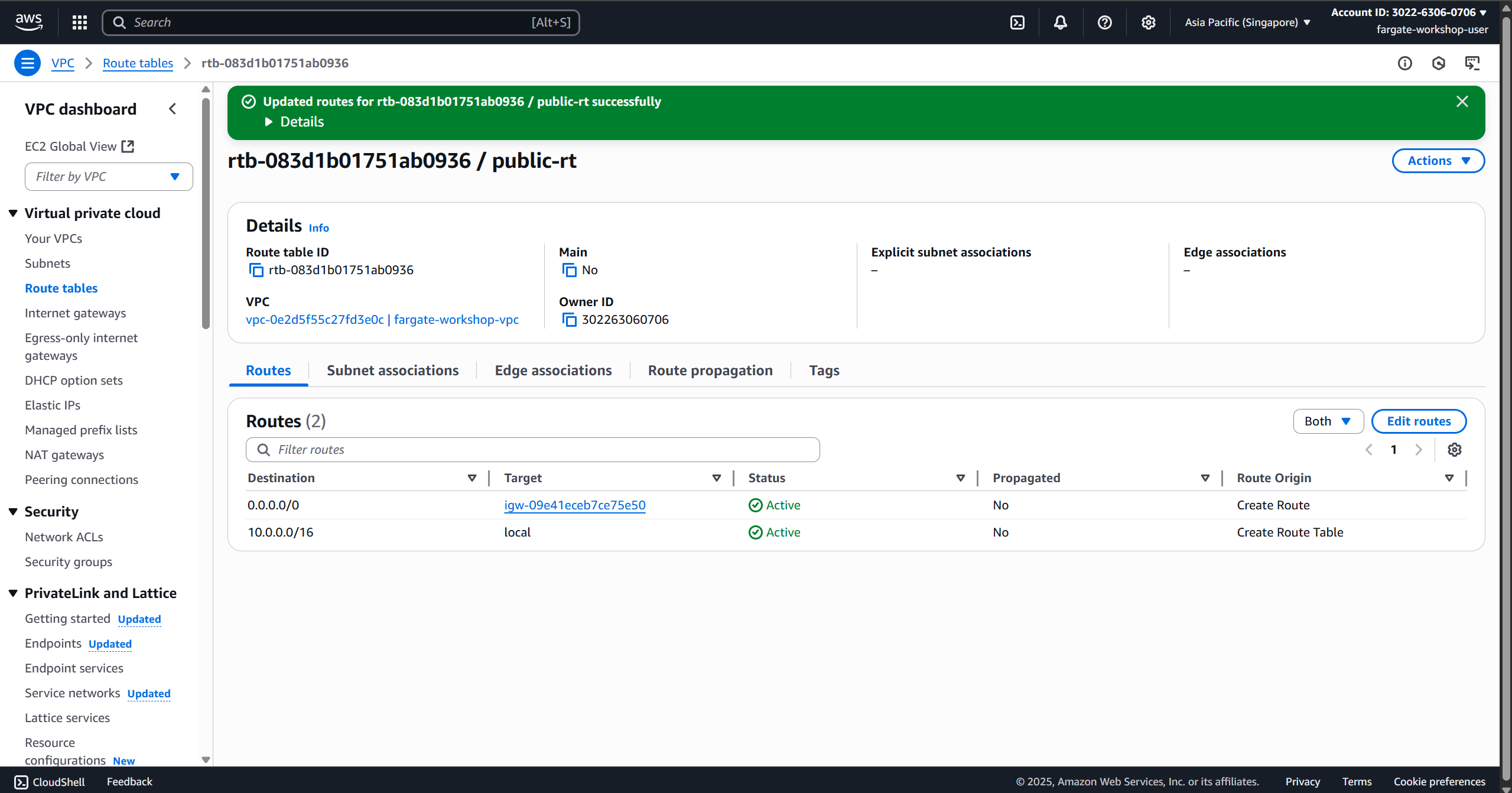
- Public Route Table:
- Route:
0.0.0.0/0→ Internet Gateway - Associate with Public Subnet 1 & 2
- Route:
- Private Route Table AZ1:
- Route:
0.0.0.0/0→ NAT Gateway AZ1 - Associate with Private Subnet 1
- Route:
- Private Route Table AZ2:
- Route:
0.0.0.0/0→ NAT Gateway AZ2 - Associate with Private Subnet 2
- Route:
Create Security Groups
- ALB Security Group:
- Inbound: TCP 80, 443 from
0.0.0.0/0 - Outbound: Allow all
- Inbound: TCP 80, 443 from
- Fargate Tasks Security Group:
- Inbound: TCP 8080 from ALB SG
- Outbound: Allow all
- Database Security Group (if using Aurora/DynamoDB in Private Subnet):
- Inbound: 3306 (Aurora) from Fargate SG
- Outbound: Allow all
Expected Result
You should now have a network structure with:
- VPC 10.0.0.0/16
- 2 Public Subnets (AZ1, AZ2) + 2 Private Subnets (AZ1, AZ2)
- Internet Gateway for Public Subnets
- NAT Gateway for Private Subnets
- Properly configured Route Tables
- Separate Security Groups for ALB, Fargate, and Database